Defences available:
Security Training

£20,000
Asset Audit

£30,000
Antivirus
£30,000
Network Monitoring (Plant)

£50,000
CCTV (Plant)
£40,000
Firewall (Plant)

£30,000
CCTV (Office)

£40,000
Firewall (Office)

£30,000
Network Monitoring (Office)

£50,000
Database Encryption

£20,000
PC Upgrade

£30,000
PC Encryption

£20,000
Controller Upgrade
£30,000
Server Upgrade
£30,000
Threat Assessment

£20,000
Network Segmentation
£30,000













Defences to play:
0 Points
Year 1
Funds remaining:
£100,000
Defences Played:
Security Training

£20,000
A quick yet thorough one-day introduction on security essentials for all employees.
Security training is vital for all employees in at-risk organisations, even if they are not a part of the cybersecurity team. One of the main causes of cyberattacks is a lack of awareness – many employees fall victim to phishing scams, which can result in serious consequences for the whole organisation. Hence, a quick course in basic cybersecurity can prevent a great deal of damage. These courses usually involve: identifying different types of threats (spam, phishing, malware, ransomware, etc.), importance of password security, policies to adhere to, data protection and identifying and reporting threats. Employees are an organisation’s first line of defence... educating them is key!
Play card
Asset Audit

£30,000
The entire infrastructure is thoroughly assessed for unknown assets and associated vulnerabilities. *You will be provided with more defences (cards) that you will be able to play.*
A cybersecurity asset audit acts as a checklist, thoroughly assessing the infrastructure of an organisation, checking for vulnerabilities. This will also ensure they are adhering to regulations and policies regarding their cybersecurity, and so it is important these audits are carried out regularly. The audits are usually carried out by a third party, in order to ensure there is no bias, or conflict of interest. The assets audited include: control systems, networking equipment, storage hardware, data acquisition systems, and any other assets that may be deemed vulnerable. It’s recommended that an audit is carried out at least annually, however, this will vary hugely depending on an organisation’s size, budget, risk appetite (willingness to take risk), etc.
Play card
Antivirus

£30,000
A recent, decent professional antivirus from a reputable provider is installed on the hosts.
Antivirus software is a basic cybersecurity tool. It runs in the background, detecting and dealing with viruses, worms, trojans, adware, ransomware, etc. These programs will have multiple layers of security – this is necessary considering the power of some malware nowadays. This software may be installed on computers, servers, etc. Antivirus will use numerous techniques: Virus definitions – matching a threat to a database of known virus signatures, to identify it; Heuristic detection – detecting virus families even if there is no existing signature; Behavioural blocking – identifying suspicious behaviour through keystrokes, modifying files, etc; Sandbox detection – testing programs in a separate virtual environment, before running on the actual system.
Play card
Network Monitoring (Plant)

£50,000
This big, shiny piece of bleeding-edge technology is quite expensive but also very effective.
Network monitoring is exactly what it says – monitoring the network. Software or hardware can be installed to keep track of activity on a network, including response time, uptime and availability. The monitoring allows organisations to see how the network behaves regularly, so if there is an unusual change in activity, they can quickly identify any failures or issues, such as cyberattacks. Hence, they can resolve the issue with minimal disruption. Network monitoring offers further benefits such as reducing manual work for IT staff, and highlighting parts of the network infrastructure that may need changing or upgrading.
Play card
CCTV (Plant)

£40,000
Surveillance camera and alarms that will automatically warn security guards of an intrusion.
CCTV offers excellent physical security to a business. Simply having CCTV installed is a deterrent to criminals. Having a camera watching equipment and employees at all times would certainly be useful were something bad to happen. For example, if someone plugged a malware-infested USB into a computer (maliciously or not), CCTV would be a simple way to identify said person, and at what time the incident occurred. Or, if the system for a piece of machinery was under a cyberattack and began malfunctioning, the CCTV would catch this, in case an employee was not present.
Play card
Firewall (Plant)

£30,000
A software and hardware solution that monitors and filters unauthorised traffic coming from the Internet to the plant network.
A firewall is either hardware (device between network and gateway), or software (program installed on a device), though it is obviously more effective to implement both. It monitors all incoming/outgoing traffic on a network, when it goes through the ports. It will then allow through, or discard these packets, depending on the rules specified. These rules will vary depending on the organisation, household, etc. There are various types of firewalls: packet-filtering, next generation, proxy, NAT, and stateful multilayer inspection.
Play card
CCTV (Office)

£40,000
Surveillance camera and alarms that will automatically warn security guards of an intrusion.
CCTV (closed circuit television) offers excellent physical security to a business. Simply having CCTV installed is a deterrent to (cyber)criminals. Having a camera watching equipment and employees at all times would certainly be useful were something bad to happen. For example, if someone plugged a malware-infested USB into a computer (maliciously or not), CCTV would be a simple way to identify said person, and at what time the incident occurred. Or, if the system for a piece of machinery was under a cyberattack and began malfunctioning, the CCTV would catch this, in case an employee was not present.
Play card
Firewall (Office)

£30,000
A software and hardware solution that monitors and filters unauthorised traffic coming from the Internet to the office network.
A firewall is either hardware (device between network and gateway), or software (program installed on a device), though it is obviously more effective to implement both. It monitors all incoming/outgoing traffic on a network, when it goes through the ports. It will then allow through, or discard these packets, depending on the rules specified. These rules will vary depending on the organisation, household, etc. There are various types of firewalls: packet-filtering, next generation, proxy, NAT, and stateful multilayer inspection.
Play card
Network Monitoring (Office)

£50,000
This big, shiny piece of bleeding-edge technology is quite expensive but also very effective.
Network monitoring is exactly what it says – monitoring the network. Software or hardware can be installed to keep track of activity on a network, including response time, uptime and availability. The monitoring allows organisations to see how the network behaves regularly, so if there is an unusual change in activity, they can quickly identify any failures or issues, such as cyberattacks. Hence, they can resolve the issue with minimal disruption. Network monitoring offers further benefits such as reducing manual work for IT staff, and highlighting parts of the network infrastructure that may need changing or upgrading.
Play card
Database Encryption

£20,000
Military-grade, proven encryption mechanism for all databases.
Encrypting the 'data at-rest' in a database adds a layer of security – a decryption key is needed to access the data. This key is stored elsewhere, not on the same server. Furthermore, data protection is becoming increasingly important these days. Although organisations are not explicitly required to encrypt their data, GDPR states they should have “security measures and safeguards” in order to protect personal data. A database’s job is to store data. Hence, it should be adequately secure, should a cyberattacker attempt to gain access to it. If the attacker does gain access to the data, they may use it for ransom, sell the data, etc.
Play card
PC Upgrade

£30,000
A brand new, up-to-date OS and software suite for all Computers.
Upgrading PCs will provide benefits in numerous areas, especially security. PCs nowadays are designed with security as a priority, due to the increasing prevalence of cyberattacks. They come with built-in security features. New PCs will also be more compatible with current cybersecurity products, and support for this upgraded hardware will be more available. With older systems being more vulnerable, unstable and unreliable, the cost of fixing these issues as they arise (instead of upgrading), may rack up hugely.
Play card
PC Encryption

£20,000
Military grade, proven encryption mechanism for the hard drives of all PCs.
Encrypting the data on PCs adds a layer of security – a decryption key is needed to access the data. Many PCs will come with encryption built-in, however paying for encryption may offer further, enhanced security. PC encryption encompasses file encryption, as well as 'data in-transit'. When data is travelling within and to other devices, it must be protected, to avoid cyberattackers stealing or altering the data. This could be through a man-in-the-middle attack, for example, where an attacker intrudes on communication between two parties, either to listen or alter the data. To protect data in-transit, the data will be encrypted, transferred, and then decrypted at its destination.
Play card
Controller Upgrade

£30,000
Software patches and an update to the firmware of the SCADA controller.
Upgrading the SCADA controller’s firmware may offer benefits to an organisation in many areas, including their cybersecurity. As the SCADA system is what controls all PLCs, it’s vital that this system functions well and is secure. These types of systems are closely observed and researched, as they form a part of critical national infrastructure. It has been shown that, over time, the controllers degrade, and vulnerabilities are found. In newer controllers, these vulnerabilities have been secured, there is more support available for issues and the overall cybersecurity is generally more effective.
Play card
Server Upgrade

£30,000
A brand new, up-to-date OS, web server and database management system.
Upgrading servers will improve both efficiency and security. Technology is constantly evolving –upgrading servers will provide more storage, less downtime, etc. Cyberattacks are also becoming more prevalent and powerful. Nowadays, new server technology takes this into account, by building in features that will help to prevent/minimise the risk of cyberattacks. Increasing the cybersecurity of a system is known as system hardening. This may include: encryption for communication, removal of unnecessary software, updating operating systems, strong password complexity, intrusion detection systems and data back-ups.
Play card
Threat Assessment

£20,000
Reveals existing threats to the company, and helps provide a recommendation to most effectively protect against your threats. *You will be recommeneded a defence that you should think about playing.*
A threat assessment provides details of any existing threats to an organisation. After this, a risk management plan may be created, taking into account the vulnerabilities discovered. High-value data is identified, such as customer/staff information, patented/secret data, information that may damage reputation, etc. Assets analysed include: software/hardware, IT policies, network architecture, data storage, environmental/physical security controls, etc. The organisation must also realise that, although external threats can be menacing, often there are internal threats, intentional or unintentional, that can cause them a great deal of damage. Hence, the risk management plan resulting from the threat assessment may suggest: data handling policies, security training, disaster recovery procedures, etc.
Play card
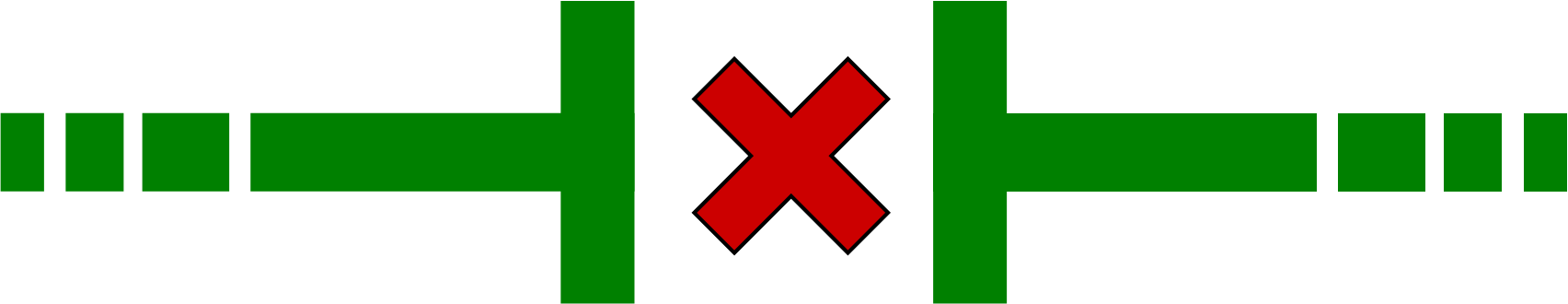
Network Segmentation

£30,000
Restricts or even stops traffic flow between the Office, Plant and Safety System to make it harder for attackers to move around the network.
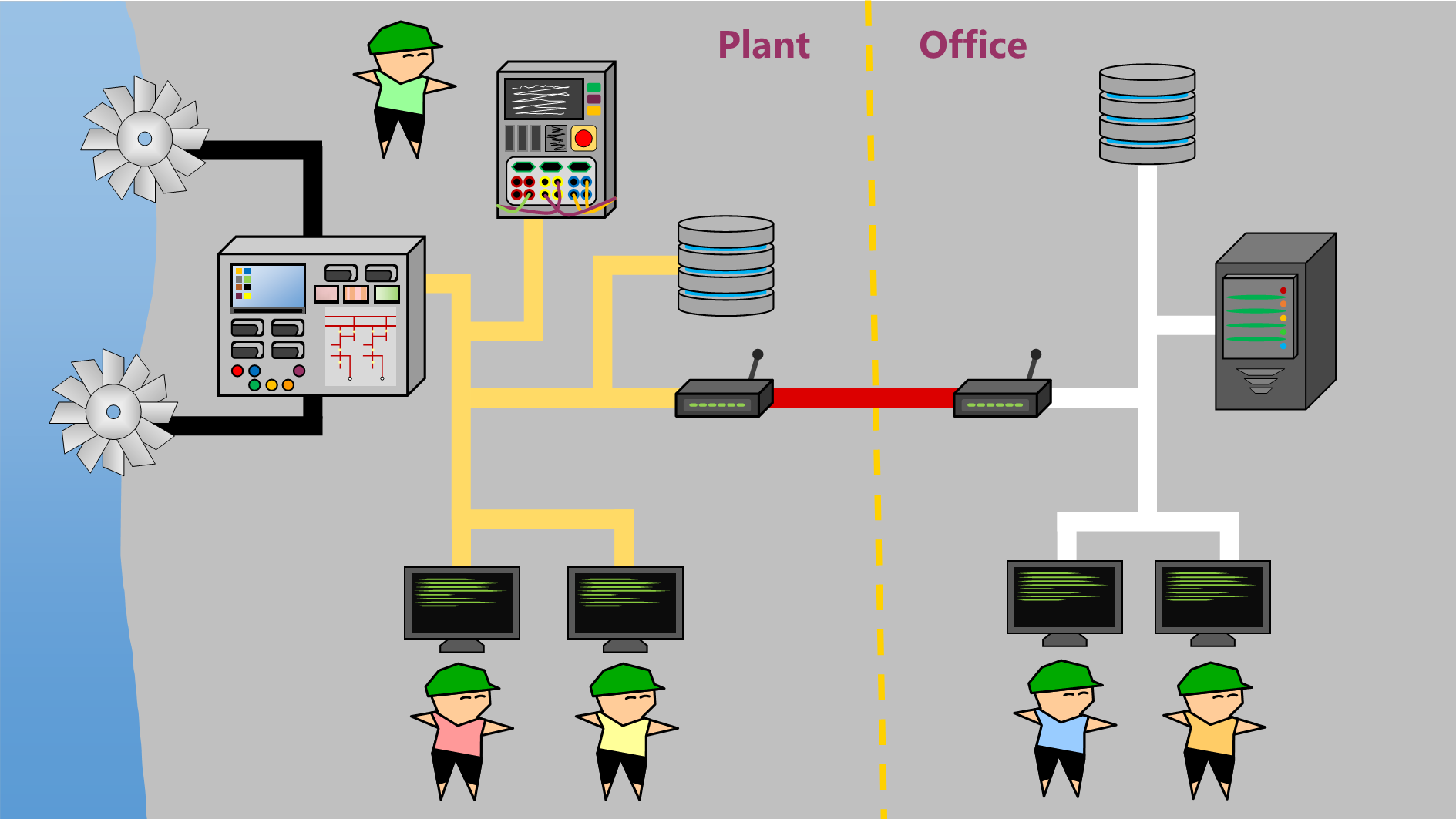
In ICS environments, network and device segmentation is important for security. It’s a security measure that prevents a hacker from easily travelling through a network. Without system segmentation, if a hacker gains access to the system, they have the potential to “hack their way” through. However, by separating the systems, physically or logically, the hacker can no longer travel between sections of the network. At the very minimum, the OT network of a hydroplant should be separated from the corporate IT network. But this separation should ideally go further. The network that runs the business-as-usual processes may be separated from their back-up systems – so should the hacker gain access and interfere with the main systems, the back-up systems can protect these processes. This could save the organisation from a lot of damage.
Play card
Intrusions and Impact
Congratulations on your new job as Head of Cyber Security at AquaVolt Power!
You'll be on-site at our hydro-electric power plant for four years, and you'll get a budget of £100,000 per year to install and upgrade our Cyber Security systems. Remember - your decisions are the only things between our power plant and all the viruses, hackers, and organised criminals out there. Think strategically!
Four Years
£100,000 Pounds
Can you keep the plant safe?
Let's Play!
Consequences
You have reached the end
